When analyzing malware using behavioral techniques, it’s often useful to intercept network connections in your lab. Since malicious software commonly uses hostnames when communicating with network resources, you can redirect such connections by defining the desired hostname to IP address mapping. Here are 3 free tools that can make it easy to accomplish this.
Rather than providing the malicious program the IP address of the actual host it’s trying to access, you can provide the IP address of an internal laboratory system. It’s possible to define this mapping in the “hosts” file on the infected laboratory computer. Alternatively, you can use a DNS server provide falsified DNS responses to queries. If you don’t want to configure a full-blown DNS server, you can use specialized tools such as ApateDNS, FakeDNS and fakeDNS.py.
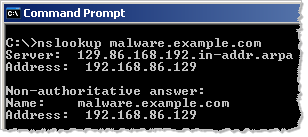
ApateDNS in Action on Windows
Mandiant recently released a Windows tool called ApateDNS, written by Steve Davis. ApateDNS’s DNS responses will specify the desired IP address of your choosing, regardless of which hostname is being resolved. The tool logs all DNS queries it processes.
To use ApateDNS, you’ll need to point your infected laboratory system to the host where ApateDNS is running. In most scenarios, though, you’ll probably run ApateDNS directly on the infected host. While the tool attempts to automatically configure your local system to use localhost as the DNS server while ApateDNS is running, this doesn’t always work; be prepared to manually modify your DNS settings for this purpose.
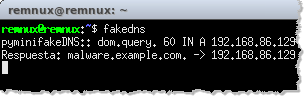
FakeDNS in Action on Windows
FakeDNS is a free Windows tool from Verisign’s iDefense group, which is part of the larger Malcode Analysis Pack distribution. Though the original Malcode Analysis Pack web page is no longer accessible, you can still download the executable’s installer file from the iDefense website.
Like ApateDNS, FakeDNS responds to all DNS queries with the specified IP address, logging the details of the received requests and transmitted responses.
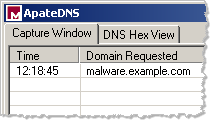
fakedns.py in Action on Linux
Another option for falsifying DNS responses in a malware analysis lab is the fakedns.py script by Francisco Santos. It’s written in Python, and will run on most platforms as long as Python is installed on the system. A version of this script is included in the REMnux Linux distribution.
The fakedns.py script is a command-line tool. By default, it will respond to DNS queries with the IP address of the host where the script is running, but this behavior can be modified using a command-line option.
To see how fake DNS servers can be used for malware analysis, take a look at my recorded Introduction to Malware Analysis webcast.
Hand-picked related posts:
- NetworkMiner for Analyzing Network Streams and Pcap Files
- Using Netsh for Easier Network Setup in a Malware Lab
- Process Monitor Filters for Malware Analysis and Forensics
轉自 http://blog.zeltser.com/post/11869187517/fake-dns-tools-for-malware-analysis





0 意見: