Safari is a web browser developed by Apple and is included as part of the Apple Macintosh OS X operating system. It has been the default browser on all Apple computers since Mac OS X version 10.3 Panther and its first public release was in 2003. Safari is currently at major version 5 released in June 2010.
In June 2007 Apple released a version of Safari for Microsoft Windows operating systems. The version of Safari at this time was version 3. Windows versions have been updated in parallel with Mac OS X versions ever since and are also at the time of writing at version 5.
As of 2011, Safari is the fourth most widely used browser in the US, following Internet Explorer, Mozilla Firefox, and Google Chrome, respectively [1] . Forensic Analysis of Safari
NetAnalysis currently supports the analysis of all versions of Safari. Safari runs on Microsoft Windows and Apple Macintosh OS X operating systems. The data created by Safari is file based and the structure of the data it creates is similar between operating systems.
Safari Browser v3 - 5
Safari, like all web browsers, aggressively prompts the user to update to the latest version to incorporate new security patches. This means that you are likely to find the most recent version on computers currently in use, which at the time of writing is Version 5.
Internet History and Cache data is stored within each users profile, the exact location will vary depending on the operating system in use.
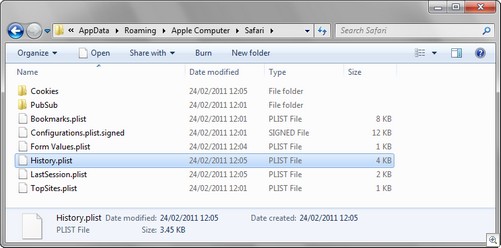
Safari stores Internet history records within an Apple property list file entitled history.plist (as shown in Figure 1). Property list files have the file extension .plist and therefore are often referred to as plist files. Plist files may be in either an XML format or a binary format. For earlier versions of Safari (both Windows and Macintosh variants) the history.plist file was in the XML format. Later and current versions utilise the binary plist format. NetAnalysis parses both the XML and binary formatted history plist files.
Figure 1
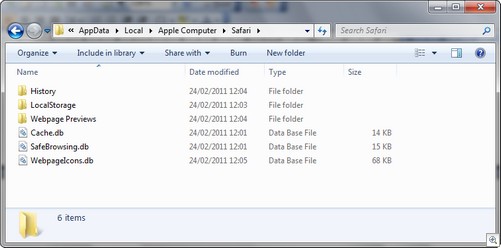
Safari versions 3 to 5 store the cache in SQLite 3 database files entitled cache.db (as shown in Figure 2). Earlier versions of Safari stored cache in files that had the file extension .cache. These files are not currently supported.
Figure 2
Stage 1 - Recovery of Live Safari Data
To process and examine Safari live Internet history and cache with NetAnalysis, the following methodology should be used. In the first instance, it is important to obtain the live data still resident within the file system (web pages can only be rebuilt from live cache data).
This can be done in either of the following three ways:
-
Export all of the data (preferably in the original folder structure) utilising a mainstream forensic tool
-
Mount the image using a forensic image tool
-
Access the original disk via a write protection device
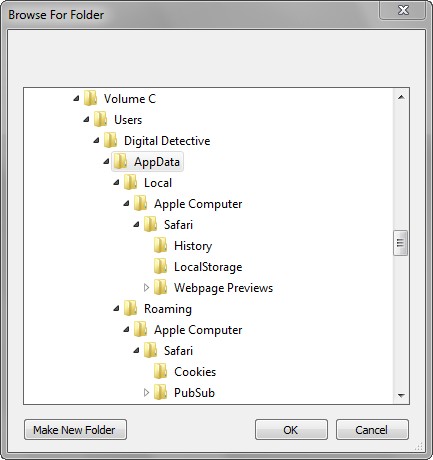
Once the data has been extracted to an export folder, open NetAnalysis and select File >> Open All History From Folder. Select the folder containing your exported Safari data.
Figure 3
Note |
Please be aware that NetAnalysis will attempt to identify and import any browser related files. If you only wish to process one specific browser type, only select the folder containing the file you wish to process, or open a specific file using File >> Open History. |
Stage 2 - Recovery of Deleted Safari Data
HstEx is a Windows-based, advanced professional forensic data recovery solution designed to recover deleted browser artefacts and Internet history from a number of different source evidence types. HstEx supports all of the major forensic image formats.
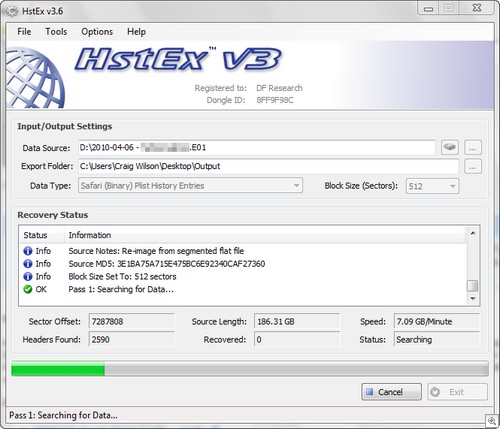
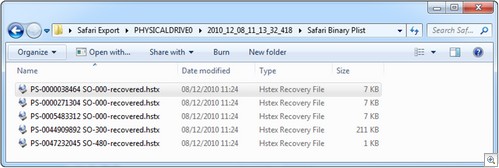
HstEx currently supports the recovery of Safari XML and Binary plist data. It cannot at the moment recover cache records (research and development is currently being conducted). Figure 4 shows HstEx processing
Figure 4
Please see the following link for information on using HstEx to recover browser data:
Please ensure you select the correct Data Type prior to processing. Safari v5 stores history data in binary plist files. When HstEx has finished processing, it will open a window similar to the one shown in Figure 5. These files can now be imported into NetAnalysis by either selecting File >> Open History and selecting all of the files, or select File >> Open All History From Folder and selecting the root recovery folder.
Figure 5
Default Folder Locations
Apple Safari data can be found in the following default folder locations:
Microsoft Windows XP
Microsoft Windows XP (History) |
\Documents and Settings\<user>\Application Data\ Apple Computer\Safari |
Microsoft Windows XP (Cache) |
\Documents and Settings\<user>\Local Settings\Application Data\ Apple Computer\Safari |
Microsoft Windows Vista / Window 7
Microsoft Windows Vista / Windows 7 (History) |
\Users\<user>\AppData\Roaming\Apple Computer\Safari |
Microsoft Windows Vista / Windows 7 (Cache) |
\Users\<user>\ AppData\Local\ Apple Computer\Safari |
Apple Macintosh OSX 10.6
Apple Macintosh OSX 10.6 (History) |
/Users/<user>/Library/Safari |
Apple Macintosh OSX 10.6 (Cache) |
/Users/<user>/Library/Caches/com.apple.Safari |
Further Reading
Posted by Digital Detective at 14:21
轉自 digital-detective